Snort:Annexes
Jump to navigation
Jump to search
Annexes
Inscription sur snort.org et récupération du oinkcode
|
1. Aller sur http://www.snort.org.
|
|
|
3. Remplir le formulaire, cocher la case « Check this… » puis cliquer sur Register.
|
|
|
5. Une fois enregistré et loggué, vous devez obtenir l’écran suivant : |
|
|
6. En bas de l’écran, cliquer sur le bouton « Get code » afin d’obtenir un oinkcode. |
Paramètres
Cartographie
La cartographie suivante présente les appels de Barnyard, Snort, Guardian et Oinkmaster avec leurs principaux paramètres. Les points qui suivent présentent l’utilisation et les listes exhaustives de ces paramètres.
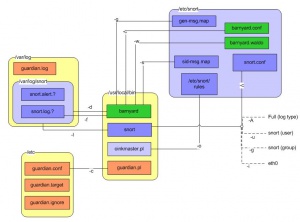
Paramètres de Snort
Usage: snort [-options] <filter options>
Options:
-A Set alert mode: fast, full, console, test or none (alert file alerts only)
"unsock" enables UNIX socket logging (experimental).
-b Log packets in tcpdump format (much faster!)
-B <mask> Obfuscated IP addresses in alerts and packet dumps using CIDR mask
-c <rules> Use Rules File <rules>
-C Print out payloads with character data only (no hex)
-d Dump the Application Layer
-D Run Snort in background (daemon) mode
-e Display the second layer header info
-f Turn off fflush() calls after binary log writes
-F <bpf> Read BPF filters from file <bpf>
-g <gname> Run snort gid as <gname> group (or gid) after initialization
-G <0xid> Log Identifier (to uniquely id events for multiple snorts)
-h <hn> Home network = <hn>
-H Make hash tables deterministic.
-i <if> Listen on interface <if>
-I Add Interface name to alert output
-k <mode> Checksum mode (all,noip,notcp,noudp,noicmp,none)
-K <mode> Logging mode (pcap[default],ascii,none)
-l <ld> Log to directory <ld>
-L <file> Log to this tcpdump file
-M Log messages to syslog (not alerts)
-m <umask> Set umask = <umask>
-n <cnt> Exit after receiving <cnt> packets
-N Turn off logging (alerts still work)
-o Change the rule testing order to Pass|Alert|Log
-O Obfuscate the logged IP addresses
-p Disable promiscuous mode sniffing
-P <snap> Set explicit snaplen of packet (default: 1514)
-q Quiet. Don't show banner and status report
-r <tf> Read and process tcpdump file <tf>
-R <id> Include 'id' in snort_intf<id>.pid file name
-s Log alert messages to syslog
-S <n=v> Set rules file variable n equal to value v
-t <dir> Chroots process to <dir> after initialization
-T Test and report on the current Snort configuration
-u <uname> Run snort uid as <uname> user (or uid) after initialization
-U Use UTC for timestamps
-v Be verbose
-V Show version number
-w Dump 802.11 management and control frames
-X Dump the raw packet data starting at the link layer
-y Include year in timestamp in the alert and log files
-Z <file> Set the performonitor preprocessor file path and name
-? Show this information
<Filter Options> are standard BPF options, as seen in TCPDump
Longname options and their corresponding single char version
--logid <0xid> Same as -G
--perfmon-file <file> Same as -Z
--pid-path <path> Specify the path for the Snort PID file
--snaplen <snap> Same as -P
--help Same as -?
--version Same as -V
--alert-before-pass Process alert, drop, sdrop, or reject before pass, default is pass before alert, drop,...
--treat-drop-as-alert Converts drop, sdrop, and reject rules into alert rules during startup
--process-all-events Process all queued events (drop, alert,...), default stops after 1st action group
--dynamic-engine-lib <file> Load a dynamic detection engine
--dynamic-engine-lib-dir <path> Load all dynamic engines from directory
--dynamic-detection-lib <file> Load a dynamic rules library
--dynamic-detection-lib-dir <path> Load all dynamic rules libraries from directory
--dump-dynamic-rules <path> Creates stub rule files of all loaded rules libraries
--dynamic-preprocessor-lib <file> Load a dynamic preprocessor library
--dynamic-preprocessor-lib-dir <path> Load all dynamic preprocessor libraries from directory
--dump-dynamic-preproc-genmsg <path> Creates gen-msg.map files of all loaded preprocessor libraries
--create-pidfile Create PID file, even when not in Daemon mode
--nolock-pidfile Do not try to lock Snort PID file
--disable-inline-initialization Do not perform the IPTables initialization in inline mode.
--pcap-single <tf> Same as -r.
--pcap-file <file> file that contains a list of pcaps to read -read mode is implied.
--pcap-list "<list>" a space separated list of pcaps to read - read mode is implied.
--pcap-dir <dir> a directory to recurse to look for pcaps - read mode is implied.
--pcap-filter <filter> filter to apply when getting pcaps from fileor directory.
--pcap-no-filter reset to use no filter when getting pcaps from file or directory.
--pcap-loop <count> this option will read the pcaps specified oncommand line continuously.
for <count> times. A value of 0 will read until Snort is terminated.
--pcap-reset if reading multiple pcaps, reset snort to post-configuration state before reading next pcap.
--pcap-show print a line saying what pcap is currently being read.
--exit-check <count> Signal termination after <count> callbacks from pcap_dispatch(), showing the time it
takes from signaling until pcap_close() is called.
Paramètres de Barnyard
Usage: barnyard [OPTIONS]... (continual mode) or: barnyard -o [OPTIONS]... FILES... (batch mode) Options: -h Show this help information -? Show this help information -V Show version and exit -R Display processed configuration and exit General Configuration Options: -c <file> Use configuration file <file> -d <dir> Read spool files from <dir> -L <dir> Write output files in <dir> -v Increase the verbosity level by 1 -s <file> Read the sid-msg map from <file> -g <file> Read the gen-msg map from <file> -p <file> Read the classification map from <file> Continual Processing Mode Options: -a <dir> Archive processed files to <dir> -f <base> Use <base> as the base unified filename -n Only process new events -w <file> Enable bookmarking using <file> -D Run in daemon mode -X <file> Use <file> as the pid file Batch Processing Mode Options: -o Enable batch processing mode
Paramètres de Guardian
Usage: guardian.pl [-hd] <-c config> Options: -h shows help -d run in debug mode (doesn't fork, output goes to STDOUT) -c specifiy a configuration file other than the default (/etc/guardian.conf)
Paramètres de Oinkmaster
Usage: oinkmaster.pl -o <outdir> [options]
<outdir> is where to put the new files.
This should be the directory where you store your Snort rules.
Options:
-b <dir> Backup your old rules into <dir> before overwriting them
-c Careful mode (dry run) - check for changes but do not update anything
-C <file> Use this configuration file instead of the default
May be specified multiple times to load multiple files
-e Enable all rules that are disabled by default
-h Show this usage information
-i Interactive mode - you will be asked to approve the changes (if any)
-m Minimize diff when printing result by removing common parts in rules
-q Quiet mode - no output unless changes were found
-Q Super-quiet mode - like -q but even more quiet
-r Check for rules files that exist in the output directory
but not in the downloaded rules archive
-s Leave out details in rules results, just print SID, msg and filename
-S <file> Look for new variables in this file in the downloaded archive instead
of the default (snort.conf). Used in conjunction with -U.
May be specified multiple times to search multiple files.
-T Config test - just check configuration file(s) for errors/warnings
-u <url> Download from this URL instead of URL(s) in the configuration file
(http|https|ftp|file|scp:// ... .tar.gz|.gz, or dir://<dir>)
May be specified multiple times to grab multiple rules archives
-U <file> Merge new variables from downloaded snort.conf(s) into <file>
-v Verbose mode (debug)
-V Show version and exit
|
Script de démarrage automatique
|
[Sommaire] |
[Suivant]
Gérer les exceptions de règles
|



